-
Templarbit launches in Docker Store
Our team at Templarbit has been using Docker since 2013 and contributed to the Docker community and ecosystem early on. For example, I started...
May 2, 2018 -
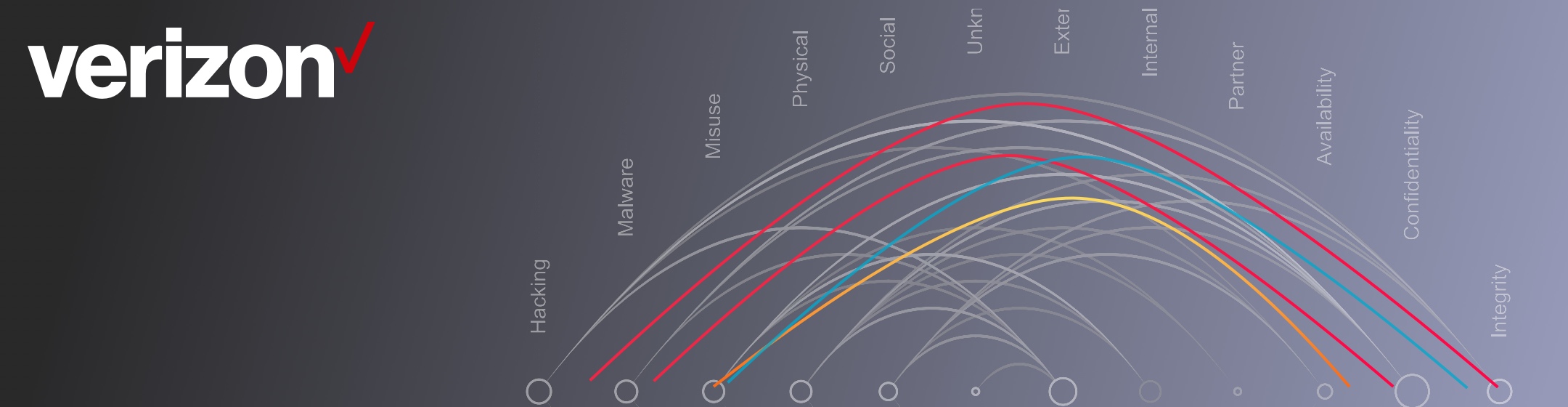
Highlights of the Verizon 2018 Data Breach Investigations Report
Verizon just published the 11th edition of its Data Breach Investigations Report. The report is comprised of real-world data breaches and...
April 11, 2018 -

HIMMS Survey: State of cyber security in health care 2018
Each year, HIMSS (Healthcare Information and Management Systems Society) conducts a survey on the state of cybersecurity in the healthcare...
April 2, 2018 -

Tracking Users with CSS
In early 2018, a physics student named Jan Böhmer created a website that tracks and records user data including clicks, mouse movements, browser...
March 20, 2018 -
Content Security Policy with Ruby on Rails
The best solution to protect your Rails app from Cross-site Scripting (XSS) attacks is to deploy a Content Security Policy (CSP). A CSP is...
March 14, 2018 -

OWASP Top 10 compared to SANS CWE 25
The Common Weakness Enumeration (CWE) is a list of software security vulnerabilities found all throughout the software development industry...
February 8, 2018 -

The best way to deploy Content Security Policy Headers and protect your application from XSS attacks
Web Applications are a popular target for attackers and often the origin of a breach. The most common security flaw seen here are Cross-site...
January 22, 2018 -

API Security Checklist
Modern web applications depend heavily on third-party APIs to extend their own services. However, an Akana survey showed that over 65% of...
January 10, 2018 -

The OWASP Top 10: 2013 vs. 2017
Every few years, the Open Web Application Security Project (OWASP) releases a list of 10 critical security risks for web applications. This...
December 14, 2017