HIMMS Survey: State of cyber security in health care 2018

Each year, HIMSS (Healthcare Information and Management Systems Society) conducts a survey on the state of cybersecurity in the healthcare industry. This survey provides insight into the threats organizations face today, their current security practices, and the future of healthcare cybersecurity.
The recently published 2018 survey was conducted on 239 IT professionals involved in their organization’s day-to-day security operations. The majority of the respondents were in management positions (36.8% executive and 37.2% non-executive) and were either primarily responsible (41.2%) or were somewhat responsible (32.6%) for their organization’s cybersecurity program.
Attackers are Targeting Healthcare
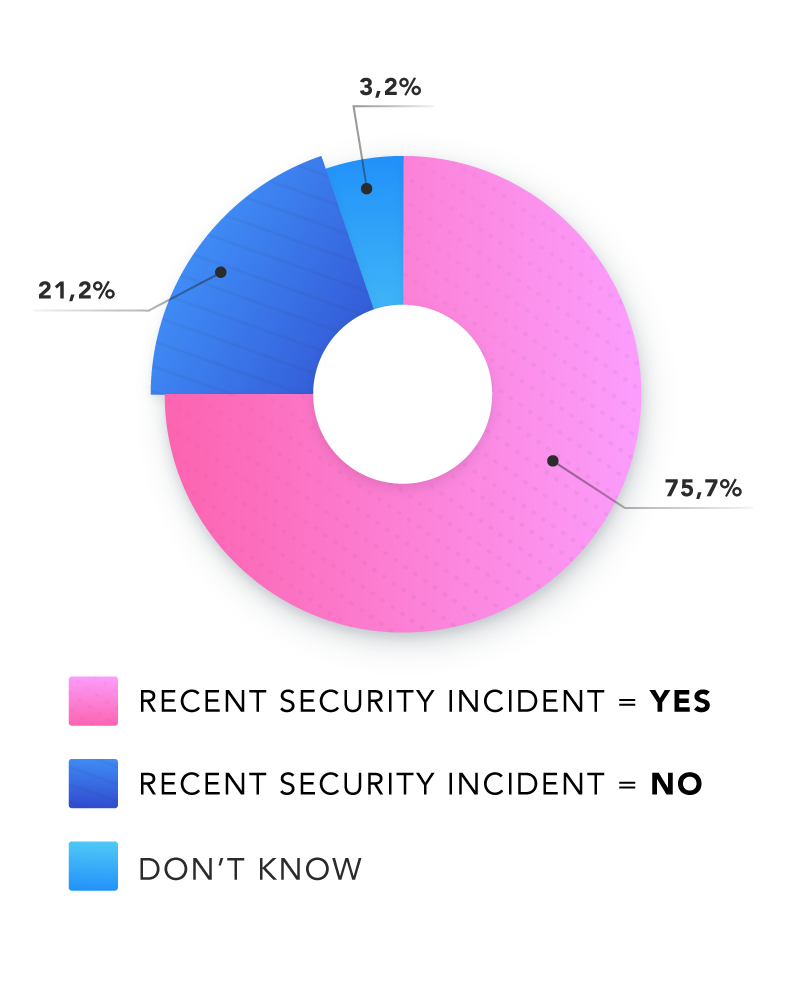
Healthcare organizations are facing an increasing number of threats. In the past 12 months, 75.7% of respondents experienced a significant security incident, while only 21.2% did not. 37.6% of these incidents were caused by online scammers. Email was the most popular attack vector, accounting for 61.9% of intrusions.
A large percentage of these incidents were discovered internally: 40.7% by security teams, and 27.5% by non-security personnel. 47.1% of these incidents were detected within 24 hours, and 60.3% were detected within the first two days.
However, there is room for improvement. 4% of respondents couldn’t identify the primary threat actor, 11.6% couldn’t identify the primary intrusion point, and 7.4% were unsure how long it took to detect an intrusion.
More Resources are Going Towards Cybersecurity
Although the incident rate has increased since the 2017 report, so has the amount of resources allocated towards cybersecurity programs. 84.3% of respondents had their organizations contribute more resources to cybersecurity, while only 3.3% had fewer resources. Most organizations (55.8%) dedicated part of their IT budget to cybersecurity, and 26.5% spent money but had no specific budget. 2.8% spent no money whatsoever on cybersecurity.
Organizations Benefit from Regular Risk Assessments
Most organizations conduct regular risk assessments. 45.5% conduct at least one assessment annually, 5.6% biannually, 10.7% quarterly, 9% monthly, and 9.6% daily. 81.3% assess cybersecurity policies and procedures, 74.7% assess the network, 73.5% assess security awareness and training programs, 71.1% assess physical security, and 69.3% perform asset inventories.
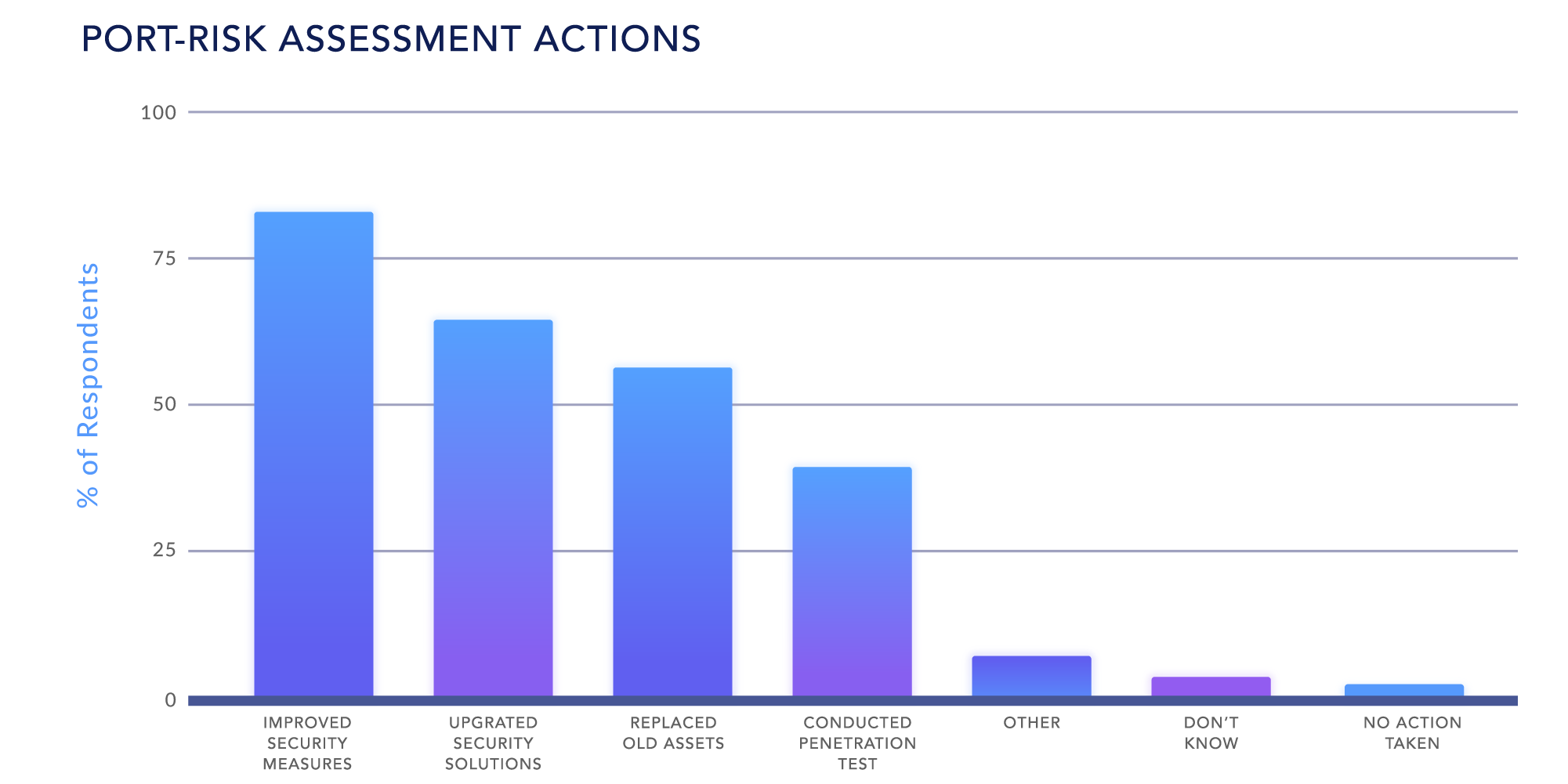
The results of these assessments helped organizations improve their cybersecurity practices, 83.1% adopted new or improved security measures, 65.1% replaced or upgraded security solutions, and 56.6% replaced outdated assets such as hardware, software, and devices. Only 2.4% deemed no further actions were necessary.
However, 5.1% of respondents didn’t conduct risk assessments at all, and 14.6% either conduct risk assessments every 2+ years or didn’t know how frequently they conducted assessments. Only 25.9% of respondents performed a comprehensive or end-to-end analysis.
Organizations Aren’t Prepared for Threats
Many respondents felt they didn’t have the resources to adequately resolve and mitigate cybersecurity threats. The biggest barriers were a lack of cybersecurity personnel (52.4%); a lack of financial resources (46.6%); and too many application vulnerabilities, endpoints, and emerging threats to keep track of (83.1%). Other factors included a lack of threat intelligence (23.3%), complex network infrastructures (20.6%), and inadequate tools or expertise to implement a solution (16.9%).
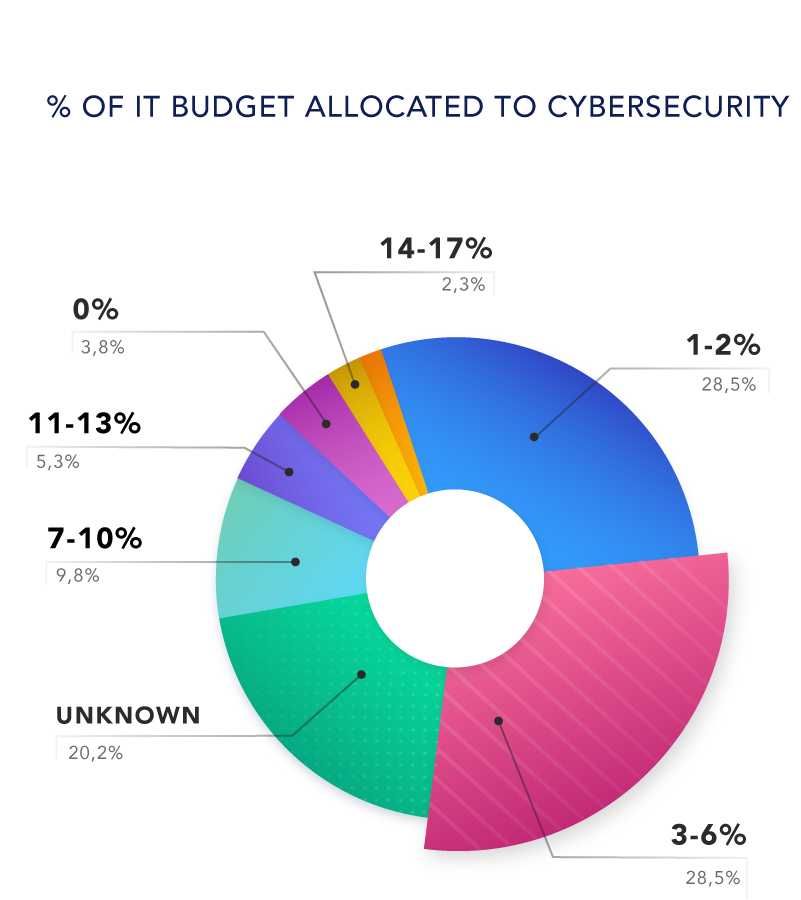
Part of the problem is budgeting. 42% of respondents spent 6% or less of their IT budget on cybersecurity, and 26.7% had no specific budget outlined. 2.8% spent no money whatsoever on cybersecurity.
Although many organizations used a security framework, there was no universally accepted framework. NIST (57.9%), HITRUST (26.4%), Critical Security Controls (24.7%), ISO (18.5%), and COBIT (7.3%) were the most common frameworks used. 16.9% of respondents had no security framework, and 8.4% were unsure what framework they had in place if any.
In addition, organizations didn’t use the same sources when learning about cyber threats. 68.6% learned about threats through word of mouth, 60% from US CERT alerts, 53.8% from HIMSS, and 47.6% through third party vendors not specific to healthcare.
Organizations Are Focusing on Incident Response, Risk Assessments, and Business Continuity
The biggest threats organizations faced were data breaches (11.8%), ransomware (11.3%), and credential stealing malware (11%). In addition, connected medical devices became an even bigger target for attackers. The top concerns for medical devices were patient safety (35.3%), data breaches (23.5%), and the device spreading malware across the network (12.4%).
When prioritizing issues for the future, respondents split the top 3 issues almost evenly between incident response (11.9%), risk assessment (11.9%), and business continuity (52.9%). 52.9% listed security as a priority, which included cloud security, website security, physical security, information sharing, and medical device security.
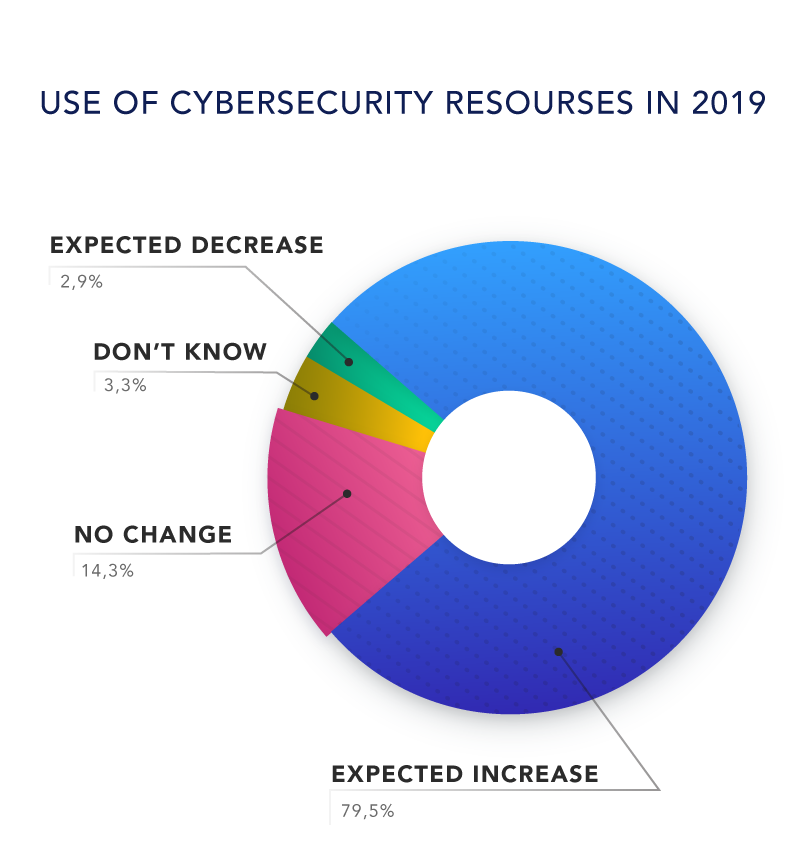
Fortunately, the majority of respondents expected their organizations to contribute more resources towards cybersecurity in the next year. 79.5% expected the amount of resources to increase, while only 2.9% expected the amount to decrease. 14.3% expected no change.
Partner with Templarbit
Health care cybersecurity is improving, but many organizations are still poorly equipped. Cybersecurity isn’t just important for protecting the organization, but for protecting patients and their data as well.
Templarbit is taking a novel approach to secure healthcare providers’ mission-critical assets. We deliver real-time, actionable insights by collecting and analyzing signals across the software application layer. Through Artificial Intelligence and proprietary machine learning models, Templarbit’s AppSec Intelligence Platform detects, blocks, monitors and reports any malicious activity.
Let’s start a conversation about how Templarbit can protect you without losing DevOps Agility in a Multi-Cloud world. You may reach me directly at our contact form. Ask me about Templarbit’s security assessment, too.
You can view the full 2018 report at himss.org.
